Microsoft is now releasing the update KB5004945 to address the PrintNightmare vulnerability for Windows 10 21H1, 20H2, and 2004 outside of their regular schedule.
The software behemoth has admitted to a serious flaw in the Windows Print Spooler service known as CVE-2021-34527. This flaw enables malicious code to be executed by attackers, giving them the power to install programs, establish new administrator accounts, and access data without the user’s permission.
The methods to temporarily disable the service and another set of instructions to configure a Group Policy Object to prevent inbound connections to a print server are two solutions that Microsoft offered as soon as the vulnerability was confirmed.
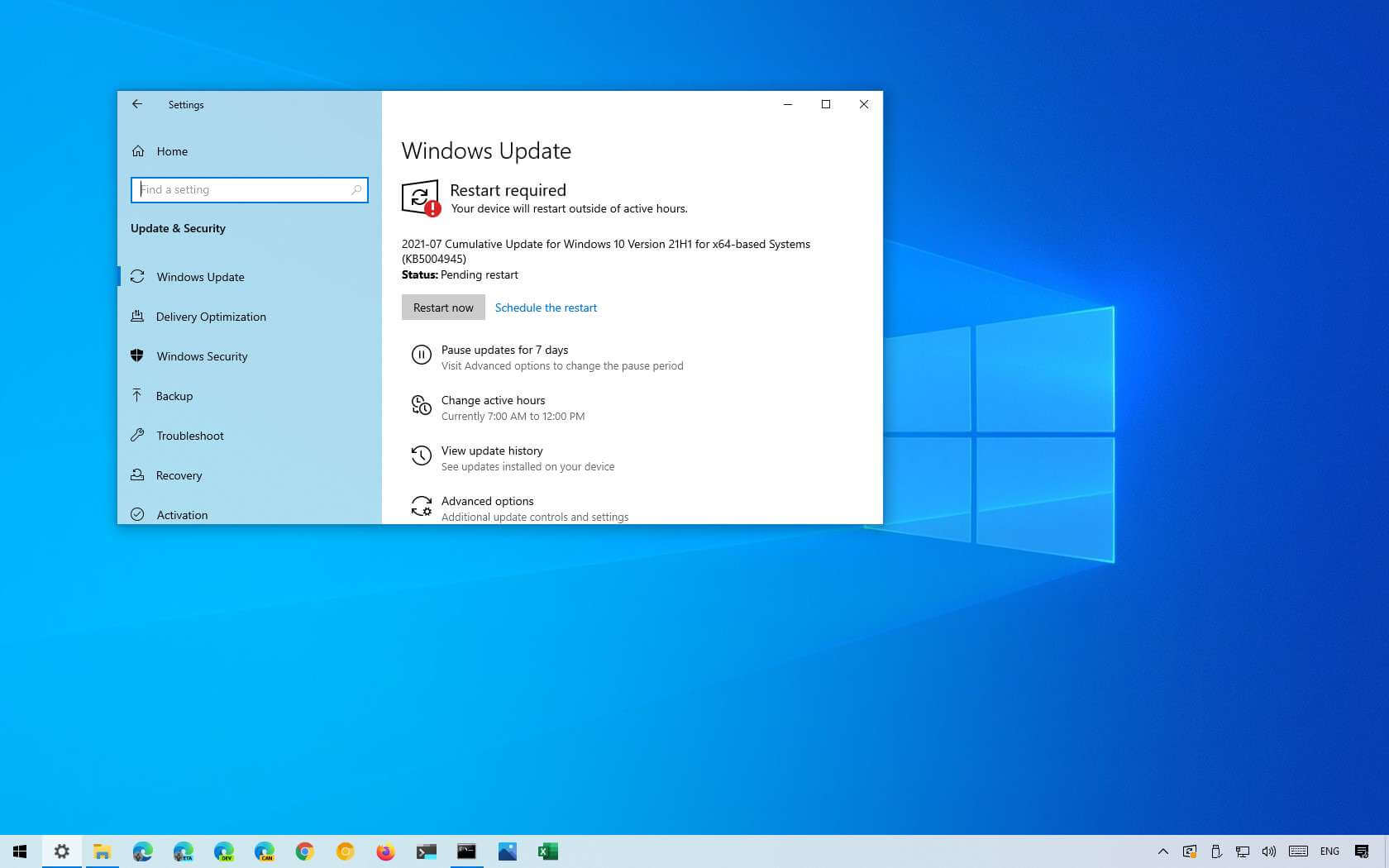
The PrintNightmare vulnerability on Windows 10 21H1, 20H2, 2004, and previous versions has been permanently fixed by the business with the release of update KB5004945, which raises the version numbers to 19041.1083, 19042.1083, and 19043.1083, respectively.
The literature states that in order to fix the vulnerability, users who are not administrators can only install signed print drivers to a print server after installing the update. Administrators have the ability to install both signed and unsigned printer drivers on a print server by default. Signed drivers are trusted by the root certificates that are installed in the system’s Trusted Root Certification Authorities.
Microsoft considers this issue to be serious and advises updating all impacted systems (clients and servers), beginning with those serving as print servers.
The same update is also accessible for Windows 10 version 1909 as KB5004946. The update is known as KB5004947 for version 1809 and KB5004950 for the first release of the operating system.
This out-of-band patch can be installed by selecting Settings>Update & Security>Windows Update and then selecting the “Check for updates” button.
The standalone version of the update is also available on the Microsoft Update Catalog website.